Memcached Amplication DDOS Attack
Memcached – a Web-based massive memory cache just like Redis and Varnish for database-driven sites such as popular Content Management System WordPress, Joomla, and Drupal, that caches the most frequently retrieved data and keeps it in memory rather than getting it from the hard disk over and over again. It is a combination of open-source software and standard server hardware that consists of memory, memory, and more memory. In short, it helps speed up the website loading speed.
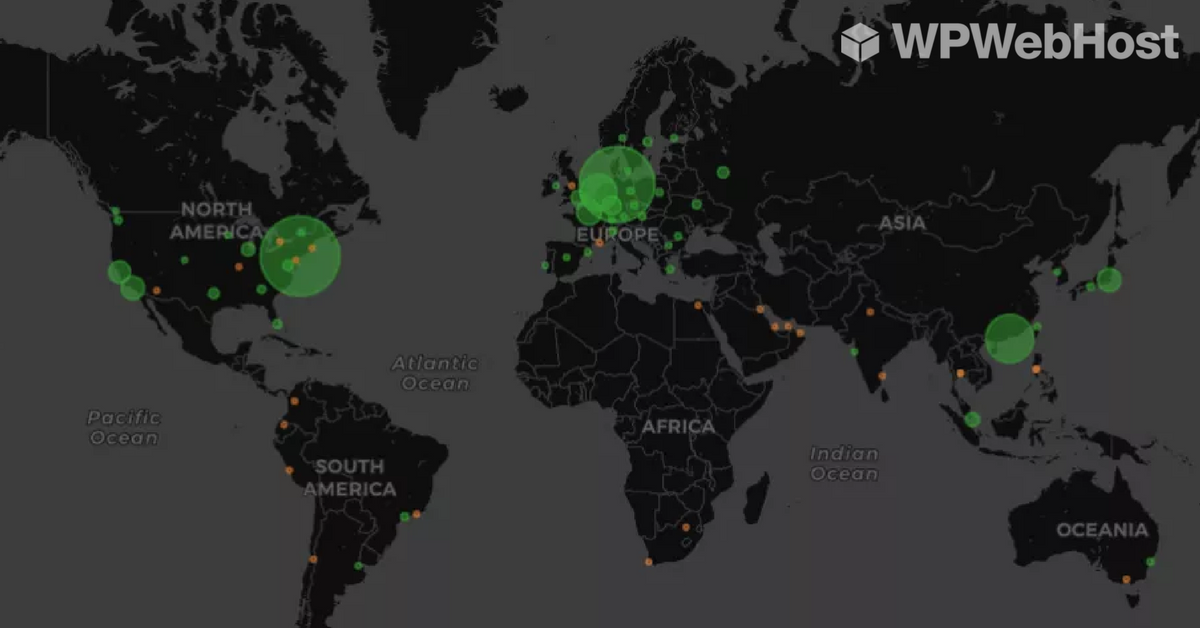
Over the last few days, Memcached has been exposed to a vulnerability risk of being used as a tool to launch a massive Amplication DDOS attack.
The way all amplication attack works are the same. The attacker launches an IP spoofing by sending forged requests to a vulnerable UDP server. The UDP server without having the ability to know if the request is legitimate will process the request. The problem happens when thousands of responses are delivered to an unsuspecting target host, overwhelming its resources – most typically the network itself.
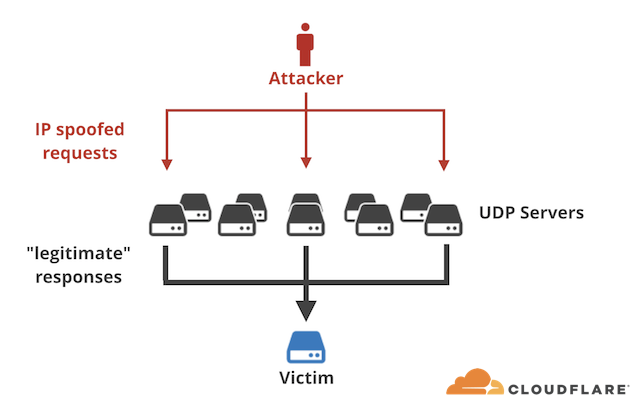
The implication for the amplication attack can be significant as it can generate a large amount of packets to take down any targeted network or websites.
WordPress on Memcached
If you manage your own WordPress website with memcached install, it’s good that you take additional steps to lock down your memached server as below:
- Lock down your firewall by setting the rules to deny all inbound TCP and UDP to port 11211.
- Start your memcached server without the UDP protocol by passing a -U 0 and listen to the only localhost.
- Upgrade your memached installation to latest 1.5.6 that will help to disable the UDP by default.
Cloudflare has posted a detailed analysis of the attack on where they have seen most of the attacks are being originated from.
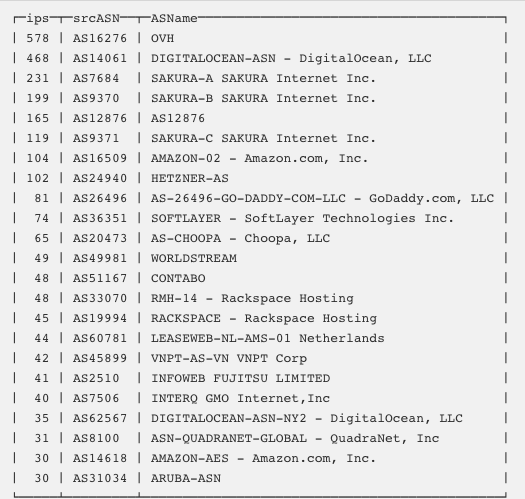
If you run your WordPress on any of the providers above, it’s good to take immediate actions as suggested above to lock it down.



